Foreign Intelligence Surveillance Act
 From Conservapedia - Reading time: 17 min
From Conservapedia - Reading time: 17 min
The Foreign Intelligence Surveillance Act (FISA) of 1978 with amendments is a post-Watergate era reform which was intended to prescribe procedures for granting quasi-judicial authorization for electronic surveillance of persons engaged in espionage, terrorism, weapons or narcotics trafficking. Critics have raised serious questions regarding the protection of Americans' 4th Amendment rights – the right to be secure in your person and effects – in relation to the law.
Under FISA, if the government makes certain allegations,[1] an American citizen and his or her entire network of personal and electronic contacts, and your contacts' contacts, can be striped of your constitutional rights of due process, right to counsel, and the right to face your accusers by a court, meeting in secret, without you ever being notified what has happened.
Former U.S. Attorney and National Review journalist covering national security Andrew McCarthy writesFISA authorities are not criminal-law authorities. It is not just that FISA is not designed to ferret out evidence of crime; it is not permitted to be used for that purpose. FISA’s objective is the collection of foreign intelligence, the gathering of information about the actions and intentions of foreign powers that may threaten American interests.[2]
There exists within the statute a potential that allows for domestic spying on political opponents similar to the abuses which toppled President Richard Nixon.[3] Such abuses, and more,[4] have in fact occurred against the campaign of Donald Trump during the Presidency of Barack Obama.[5] Abuses such as spying on members of Congress,[6] congressional committees tasked with overseeing agencies that administer the law,[7] the Supreme Court,[8] intimidation of journalists for reporting on the FISA law,[9] and blackmail are either known to have occurred or potentially exist under the law.[10] In 2017 the FBI said they could not assure that the hundreds of people administering programs created by the law would be investigated for felony criminal abuses.[11]
Contents
Background[edit]
Wiretap Act of 1968[edit]
Title III of The Omnibus Crime Control and Safe Streets Act of 1968 (Wiretap Act) is directed towards U.S. Citizens.
Title III is not to be confused with FISA Title III. Title III requires Federal, state and, other government officials to obtain judicial authorization for intercepting “wire, oral, and electronic” communications such as telephone conversations and e-mails. It also regulates the use and disclosure of information obtained through authorized wiretapping.[12]
Origins of FISA[edit]
The creation of FISA courts can be considered as a post-Watergate reform. In Watergate, a White House hired its own outside squad of "Plumbers" to "plug leaks" after it failed to get cooperation from J. Edgar Hoover due to the new 1968 Wiretap law. Hoover's FBI had a long sordid history of political spying and illegal break-ins at the request of Presidents Franklin D. Roosevelt, Lyndon Johnson, and others.[13] To rein in such governmental and extra-governmental abuses, it was thought the judicial system, or a panel of judges focused on national security, needed to sign-off on the Executive branch's use of covert activity.[14]
The use of judges for Executive branch oversight was thought to legitimize and de-politicize the issuance of surveillance warrants, rather than a congressional committee, which may be in the hands of an opposition party. Congressional committees likewise have large staffs and turnover, and the potential for leaks every two year election cycle made the idea of congressional committees approving longterm foreign surveillance operations unrealistic.
FISA courts also examine 'secret evidence'.
Modifications[edit]
As the bill's name implies, the original Act authorized procedures for granting surveillance against a foreign intelligence agency, with no provisions for non-state actors such as al Qaeda or an international drug cartel.[15][16] The 2002 Amendments to the bill allowed for these changes, although the outdated name 'Foreign Intelligence' attached to the bill's name and the FISA courts established by it remained. Furthermore, technological development expanded the meaning of the term 'wiretap'. While earlier amendments expanded the meaning beyond a microphone plant or hardwire tap on a telephone line to include satellite, microwave, and fiber-optic cables, the original law authorized 'wiretaps' only on a telephone number. With the advent of cell phones, which made it cheap and easy to change phone numbers, the authorization to 'wiretap' was changed from an electronic device to a person, regardless of what telephone or electronic source of transmission they may be using or is available for eavesdropping. Under the revisions, it is the person who is 'wiretapped', not the location or electronic device.
On October 26, 2001, Title II of the Patriot Act made significant changes to some of the original provisions of FISA. Nine months after the September 11th terrorist attack, other proposals to amend FISA were submitted. The amendments granted cross-agency intelligence sharing at their discretion.[17] Still, turf wars, competition, and mistrust between agencies exist leading to a redundancy of effort. Coordinated efforts on a target, on the other hand, can be devastating. Witness the illegal activities focused against Donald Trump and associates in 2016-18.
Snowden leaks[edit]
In June 2013, two programs operating under FISA authority were leaked to the public. The first program collects and stores in bulk domestic phone records - the number that was dialed from, the number that was dialed to, and the date and duration of the call — also known as metadata collection. It does not collect the content of those calls. The second program collects the electronic communications (phone, text, email, etc.) including content, of foreign targets. The Director of National Intelligence (DNI), the nation's supposed top intelligence official,[18] acknowledged that data is collected pursuant to Section 702 of FISA. The program may not intentionally target any person known at the time it is collected to be located in the United States, and is prohibited by Section 702,[19] but the program may incidentally collect information, including the content of phone calls, emails and texts of Americans in the United States. At the time of the Snowden leaks, as the revelations came to be called, the scope of the collection, the type of information collected, service providers involved, and the way in which it is collected remained unclear, according to Congressional Research Service,[20] the principal research and policy advisory arm of the United States Congress which authored the FISA Act and created the National Security Agency.
Since 2013, an order issued by a FISA court, has required a subsidiary of Verizon to provide a daily, on-going feed of all call detail records – including those for domestic calls – to the NSA.
The FBI/NSA database can be used in real time, or in historic mapping, to monitor people simply by entering their cell phone number and filtering the geolocation. Additionally, texts, call logs, emails, and sensitive electronic communication can all be reviewed by officials using this database.
No representation for the accused[edit]
Reform efforts in 2015 resulted in the creation of a role for an “amicus curiae,” or friend of the court, to represent the interests of the person the government wishes to surveil. The discretion to appoint an amicus curiae rests with the court.
Current law[edit]
FISA Title I and III provisions relate to the conduct of electronic surveillance and physical searches for foreign intelligence purposes of persons, facilities, or property inside the United States.
FISA Title I and Title III surveillance require there be probable cause to believe the proposed target is a foreign power or an agent of a foreign power and that the facility (can be a phone number) or place is – or is about to be – used by that target.
FISA Title I and III surveillance require formal approval from the Foreign Intelligence Surveillance Court (FISC) – also known as the FISA Court.
Title VII (Section 702) of the FISA Act provides for the most common type of FISA surveillance. Unlike Title I and Title III FISA surveillance, Section 702 collection is not subject to individual formal FISA Court approvals. Some generalized requirements for annual certification:
- The government may not intentionally target a U.S. person anywhere in the world.
- The government may not intentionally target any person known at the time of acquisition to be in the United States – FISA Title I and III are to be used.
- The government may not target someone located outside the United States for the purpose of targeting a particular, known person in this country or any U.S. person (reverse targeting).
- The government may not target for acquisition “any communication as to which the sender and all intended recipients are known at the time of the acquisition” to be in the United States.[21]
Title I authority (counterintelligence)[edit]
FISA Title I surveillance of a U.S. citizen is the most intrusive, exhaustive and far reaching type of search, seizure and surveillance authority, permitting the FBI to look at every aspect of the targets life. All communication, travel and contact can be opened and reviewed. All aspects of any of the targets engagements are subject to being secretly monitored. This is an entirely different level of surveillance authority, the highest possible, and outside FISA-702 search queries of US persons.
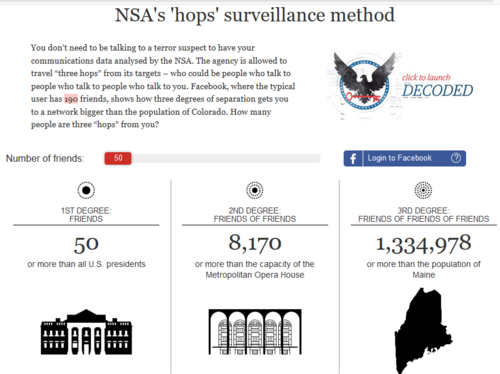
The “Title I” designation as a foreign agent applies to any action taken by the target, and auto-generates an exponential list of other people the target comes in contact with. Each of those people, groups or organizations can now have their communication reviewed, unmasked and analyzed by the DOJ/FBI with the same surveillance authority granted upon the target.
Because FISA Title I surveillance authority against a US citizen is so serious, only a few people are authorized to even apply for such surveillance warrant.
A U.S. person can be deemed the agent of a foreign power under FISA if the government shows probable cause that he or she:[22]
(A) knowingly engages in clandestine intelligence gathering activities for or on behalf of a foreign power, which activities involve or may involve a violation of the criminal statutes of the United States;(B) pursuant to the direction of an intelligence service or network of a foreign power, knowingly engages in any other clandestine intelligence activities for or on behalf of such foreign power, which activities involve or are about to involve a violation of the criminal statutes of the United States;
(C) knowingly engages in sabotage or international terrorism, or activities that are in preparation therefor, for or on behalf of a foreign power;
(D) knowingly enters the United States under a false or fraudulent identity for or on behalf of a foreign power or, while in the United States, knowingly assumes a false or fraudulent identity for or on behalf of a foreign power; or
(E) knowingly aids or abets any person in the conduct of activities described in subparagraph (A), (B), or (C) or knowingly conspires with any person to engage in activities described in subparagraph (A), (B), or (C).
FISA Title III (physical searches)[edit]
FISA Title III provides for physical searches of premises or property within the United States. Colloquilly known as a "break-in".
702 queries (Title VII)[edit]
Section 702 permits the government to target for surveillance foreign persons located outside the United States for the purpose of acquiring foreign intelligence information. However Section 702 addresses American citizens, or "US persons", caught up in foreign surveillance (incidental collection) as well. Section 702 requires "masking" a US persons identity in reports and transcripts. The FISA Court doesn't give FISA-702 “warrants”, they give FISA-702 search or surveillance approval. 702 queries are forbidden without FISA court approval. A 702(16) is a phone search query based on “TO” and/or “FROM”. A 702(17) is an email or text query based on “ABOUT”.
A FISA-702(16) Search Result would come from the FBI counter terrorism database or NSA database that returns a US person as the result of a “To” or “From” search. For example, querying phone number TO: BadGuy or FROM: BadGuy might return a list of phone numbers that also contains a US persons' phone number. That US person is protected by the Fourth Amendment. To look at the “upstream” connections of the US Person to other people, most likely other US persons and citizens, the search operator would need to ask permission of the FISA Court to review the upstream results. If the search was vital to national security, the upstream phone numbers could be reviewed without asking FISA permission first.
A FISA-702(17) Search Result would come from the FBI counter terrorism database or NSA database that returns a US person (702) as a result of an “ABOUT” (17) search. For example, querying everything in email ABOUT: BadGuy might return communication of an American who wrote a letter about BadGuy or maybe he told a friend in a text to check out a media story about BadGuy. To look at the email or text of the American, the search operator would need to ask permission of the FISA Court to see the email/text content. If the search was vital to national security, the email and text could be looked at without asking FISA permission first.
Section 702 collection is not subject to individual formal FISA Court approvals. Due to frequency of collection, instead of issuing individual court orders, the FISC approves annual certifications submitted by the Attorney General and the Director of National Intelligence that specify categories of foreign intelligence information the government is authorized to acquire.
The DOJ's National Security Division (NSD) maintains oversight of the Intelligence Agencies (such as the FBI) use of Section 702 authority. The NSD and the Office of the Director of National Intelligence (ODNI) jointly conduct reviews of the Intelligence Agencies Section 702 activities every 60 days.
The NSD – with notice to the ODNI – is required to report any incidents of Agency noncompliance or misconduct to the FISA Court.
In the Obamagate scandal,[23] 702 "About" queries are known to have occurred using the terms "Michael Cohen travel" which returned an errant result with the wrong "Michael Cohen" having traveled to Prague. Trump's lawyer provided evidence he never traveled to Prague, with other government sources corroborating the evidence. The episode proved Christopher Steele received raw FISA 702 data from the FBI, and thus the criminal conspiracy within the Obama administration to violate civil rights and interfere in the 2016 election.
John Carlin was head of DOJ's National Security Division. Surveillance of Trump and associates originated under Carlin's tenure. Carlin announced his resignation on September 27, 2016 after filing the Government's proposed 2016 Section 702 certifications on September 26, 2016. The filing did not disclose FISA abuses. Carlin was aware NSA chief Mike Rogers ordered a compliance audit which uncovered the FISA abuse. The 2016 certifications were scheduled for FISA Court approval on October 26, 2016.
Woods proceedures[edit]
Woods Procedures were named for Michael Woods, the FBI official who drafted the rules as head of the Office of General Counsel's National Security Law Unit. The goal of Woods Procedures is to ensure accuracy with regard to:
- The facts supporting probable cause.
- The existence and nature of any related criminal investigations or prosecutions involving the subject of the FISA.
- The existence and nature of any prior or ongoing asset relationship between the subject and the FBI.
They were instituted in April 2001 to “ensure accuracy with regard to … the facts supporting probable cause” after recurring instances in which the FBI had presented inaccurate information to the FISA court.[24]
Prior to Woods Procedures, “[i]ncorrect information was repeated in subsequent and related FISA packages,” the FBI told Congress in August 2003. “By signing and swearing to the declaration, the headquarters agent is attesting to knowledge of what is contained in the declaration.” The FBI's complex, multi-layered review is designed for the very purpose of preventing unverified information from ever reaching the court. It starts with the FBI field offices.
According to former FBI agent Asha Rangappa the completed FISA application requires approval through the FBI chain of command “including a Supervisor, the Chief Division Counsel (the highest lawyer within that FBI field office), and finally, the Special Agent in Charge of the field office, before making its way to FBI Headquarters to get approval by (at least) the Unit-level Supervisor there.” At FBI headquarters, an “action memorandum” is prepared with additional facts culled by analytical personnel assigned to espionage allegations involving certain foreign powers.
Next, it goes to the Justice Department “where attorneys from the National Security Division comb through the application to verify all the assertions made in it,” said Rangappa. “DOJ verifies the accuracy of every fact stated in the application. If anything looks unsubstantiated, the application is sent back to the FBI to provide additional evidentiary support – this game of bureaucratic chutes and ladders continues until DOJ is satisfied that the facts in the FISA application can both be corroborated and meet the legal standards for the court. After getting sign-off from a senior DOJ official.”
n November 2002, the FBI implemented a special FISA Unit with a unit chief and six staffers, and installed an automated tracking system that connects field offices, headquarters, the National Security Law Branch and the Office of Intelligence, allowing participants to track the process during each stage.
Starting March 1, 2003, the FBI required field offices to confirm they've verified the accuracy of facts presented to the court through the case agent, the field office's Chief Division Counsel and the Special Agent in Charge.
All of this information was provided to Congress in 2003. The FBI director at the time, Robert Mueller, also ordered that any issue as to whether a FISA application was factually sufficient was to be brought to his personal attention.[25]
Obama administration FISA abuse[edit]
- Main article: FISA abuse
Throughout the 2016 presidential election, and well into the first term of President Donald Trump, appointees of President Barack Hussein Obama illegally used the FISA process to obtain foreign intelligence surveillance warrants on domestic political opponents on behalf of the 2016 Hillary Clinton presidential campaign and the Democratic National Committee.
A FISA application alleging an American citizen and adviser to the Trump campaign was an "agent of a foreign power" was approved in October 2016,[26] granting the FBI surveillance authority under the "two hop rule" to virtually the entire Trump campaign in 50 states and the Trump transition team. Confidential screenings and interviews with cabinet appointees and staff members were surveilled by Peter Strzok and other conspirators in the FBI and DOJ, as were Oval Office conversations, briefings, and phone calls with foreign leaders after the new president was inaugurated. Many people White House staffers and personnel throughout other cabinet departments and agencies likewise had both their work and private lives subject to intense FBI intrusions well into the first eight months of the Trump presidency.
Abuses of FISA by the Deep State are the subject of the "Nunes memo" that a congressional committee voted in January 2018 to release to the public.
Contractor access[edit]
The law was circumvented by Hillary Clinton and DNC operatives who hired Fusion GPS to essentially "launder" illegally gotten raw FISA data as if it had come from outside the FBI for probable cause purposes, and was funneled back into the Obama FBI's Counterintelligence division, and the Justice Department's National Security Division, to justify FISA surveillance warrant applications of domestic political opponents. The Stormy Daniels affair, for example, arose out abuse of FISA Title I authority and had nothing to do with foreign intelligence, terrorism, narcotics or weapons smuggling.
NSA compliance audit[edit]

In the Obamagate scandal, NSA Dir. Mike Rogers discovered FISA-702(17) “About Queries” were conducted by the FBI, “contractors” and “individuals”, for reasons that had nothing to do with national security and the FBI did not notify the FISA court for approval. The FISA-702 “About Searches” returned information on Americans. Those results were passed on to people outside government. Those 702 (American Citizen) results were not “minimized” and exposed the private data of the American citizens.
In addition, Dir. Mike Rogers discovered people within the intelligence community were doing “searches” of the NSA and FBI database that were returning information that had nothing to do with “Foreign Individuals”. Rogers requested a full FISA-702 Compliance Review. As an outcome of that review, the DOJ/FBI compliance officer noted FISA violations.
These ‘passed-along’ FISA-702 search results were used by Glenn Simpson and Nellie Ohr; “unmasked” by Obama administration officials Samantha Power, Susan Rice and John Brennan, enhanced by Christopher Steele in the Steele dossier, and returned to FBI Counterintelligence Deputy Peter Strzok, DOJ Deputy Bruce Ohr, and DOJ/FBI lawyer Lisa Page, for an “insurance policy” against the election of Donald Trump.
Fraud against the court[edit]
In October 2016 the DOJ and FBI then took the Steele dossier, full circle, back to the FISA Court to gain retroactive surveillance authority and approval upon the Trump campaign and Donald Trump. Immediately after the DOJ lawyers formatted the information for a valid FISC application, the head of the DOJ National Security Division, Asst. Attn. Gen. John P Carlin, left his job. Carlin's exit came as the DOJ-NSD and NSA Dir. Mike Rogers informed the FISA court that frequent unauthorized FISA-702 searches had been conducted.
All the intelligence information the Obama DOJ and FBI collected via their illegal FISA-702 queries, combined with the intelligence FusionGPS created during their earlier contractor access to FISA-702(17) “about queries”, was the intelligence data delivered to Christopher Steele for use in creating the Steele dossier.
In March 2018, after completing an investigation into the Obama era FBI's obstruction of justice and cover up of Hillary Clinton's crimes, the Inspector General announced an investigation into Obama FISA warrant abuse.
Blackmailing Trump appointees[edit]
Because the entire Trump campaign, transition team, and administration have been the targets of fraudulent and illegal Obama administration FISA Title I survellience, President Trump has had difficulty filling and retaining appointments during his time in office.
See also[edit]
- Intelligence Community
- Obamagate timeline
- FISA abuse timeline
- Obamagate timeline 2009-2015
- Media-intelligence complex
- National Security Letter
- Warrant canary
- Michael Cohen
References[edit]
- ↑ being an "agent of a foreign power," member of a terrorist organization or drug cartel, illegal weapons smuggler, acting against the national security interests of the United States, for example.
- ↑ https://www.nationalreview.com/2018/09/trump-russia-probe-fbi-fisa-application/
- ↑ Sally Yates Should Be Investigated For Her Possible Role in Watergate-Style Surveillance, by Robert Barnes, February 15th, 2017
- ↑ Obama Has Achieved Imperial Presidency That Nixon Wanted, Jonathan Turley, April 19, 2013
- ↑ New York Times reports "In the Obama administration’s last days, some White House officials scrambled to spread information about Russian efforts to undermine the presidential election — and about possible contacts between associates of President-elect Donald Trump and Russians — across the government. [1]
- ↑ Kucinich: I Was Wiretapped As A Congressman, They Can Certainly Tap A Presidential Candidate, Ian Schwartz, March 10, 2017
- ↑ A Brief History of the CIA's Unpunished Spying on the Senate: President Obama's choice to lead the intelligence agency has undermined core checks and balances with impunity. CONOR FRIEDERSDORF, DEC 23, 2014
- ↑ Daniel Ellsberg, in responding to a question about why should people care, said: "Do they really believe that real democracy is viable, when one branch of government, the Executive, knows or can know every detail of every private communication (or credit card transaction, or movement) of: every journalist; every source to every journalist; every member of Congress and their staffs; every judge, at every level up to the Supreme Court? Do they think that every one of these people "has nothing to hide," nothing that could be used to blackmail them or manipulate them, or neutralize their dissent to Executive policies, or influence voting behavior? Is investigative journalism, or aggressive Congressional investigation of the Executive, or court restraints on Executive practices, really possible with that amount of transparency to the Executive of their private and professional lives and associations? And without any of those checks, the kind of democracy you have is that of the German Democratic Republic in East Germany, with its Stasi (which had a minuscule fraction of the surveillance capability the NSA has now, but enough to turn a fraction of the population of East Germany into secret Stasi informants)." https://freedom.press/news-advocacy/highlights-from-daniel-ellsbergas-reddit-ama-on-edward-snowden-and-nsa-surveillance/
- ↑ When can the FBI use National Security Letters to spy on journalists? That’s classified. By Trevor Timm, Columbia Journalism Review, JANUARY 11, 2016
- ↑ https://jonrappoport.wordpress.com/2017/03/18/trump-is-challenging-the-whole-cia-media-nexus/
- ↑ http://www.defenseone.com/politics/2017/03/gop-lawmaker-fbi-stop-leaks-russia-probe-or-lose-key-surveillance-tool/136325/?oref=d-topstory
- ↑ https://www.aclu.org/other/comparison-electronic-surveillance-under-title-iii-and-fisa
- ↑ Victor Laskey, It Didn't Start With Watergate, Dell, 1977, pp. 156-186
- ↑ p William C. Sullivan, “Personal Observations and Recommendations on Privacy,“ in Privacy in a Free Society, Final Report, Annual Chief Justice Warren Conference on Advocacy in the United States, June 1974.
- ↑ Executive Order 12333 issued by Ronald Reagan did allow for surveillance against non-governmental actors such as terrorist organizations and drug cartels, but it was not codified into law until the Patriot Act.
- ↑ "[Reagan] signed the order into law in 1981, giving the intelligence community the ability to extend their powers and streamlining the ability of federal agencies also investigating intelligence issues, to cooperate with the CIA requests for information. It gives the NSA almost unlimited authority to access information and intercept overseas communications. Obama sought to expand those powers and take down the wall during his second term in office. The original executive order only allowed limited personnel – those with the highest levels of security clearances – to view the original raw data. But the changes came at the end of his presidency. On Jan. 3, then-Attorney General Loretta Lynch signed the expansion of the executive order, which had already been signed by DNI Director James Clapper in mid-December. For many years the executive order didn’t draw a lot of attention, but NSA whistleblower Edward Snowden exposed its vast reach. Snowden, who is being sought by U.S. authorities for leaking classified information and is now in Russia, was the catalyst that exposed the vast authority of the NSA by revealing how the agency is capable of retrieving and storing vast amounts of what Americans considered private communications in their servers." http://circa.com/politics/some-us-intelligence-officials-want-trump-to-rescind-obamas-expansion-of-nsa-data
- ↑ Congressional Research Service, February 15, 2007
- ↑ In 2016, the Director of the FBI, James Comey, shoved aside the Attorney General and the DNI to make himself the chief spokesman of the intelligence community charged with guarding the nation's secrets.
- ↑ https://www.nsa.gov/about/civil-liberties/resources/assets/files/pclob_section_702_report.pdf
- ↑ NSA Surveillance Leaks: Background and Issues for Congress Page, Congressional Research Service, July 2, 2013
- ↑ https://www.themarketswork.com/2018/04/01/fisa-surveillance-title-i-iii-and-section-702/
- ↑ https://www.law.cornell.edu/uscode/text/50/1801
- ↑ DOJ Political Surveillance – From the IRS in 2011 to the FISA Court in 2016, Posted on March 8, 2020 by sundance. theconservativetreehouse.com
- ↑ https://fas.org/irp/agency/doj/fisa/fbi082903.pdf
- ↑ https://thehill.com/opinion/campaign/372233-nunes-memo-raises-question-did-fbi-violate-woods-procedures
- ↑ https://www.judicialwatch.org/document-archive/jw-v-doj-fisa-warrant-docs-00245/
External links[edit]
- Privacy and Civil Liberties Oversight Board, Report on the Surveillance Program Operated Pursuant to Section 702 of the Foreign Intelligence Surveillance Act, July 2, 2014
- Link to the Privacy and Civil Liberties Oversight Board site pclob.org
- The FISA Swamp, John Spiropoulos, March 3, 2020. youtube
 KSF
KSF