Proof of identity (blockchain consensus)
Topic: Finance
 From HandWiki - Reading time: 9 min
From HandWiki - Reading time: 9 min
Proof of identity (PoID) is a consensus protocol for permission-less blockchains, in which each uniquely identified individual receives one equal unit of voting power and associated rewards (minting token). The protocol is based on biometric identification, humanity identification parties and additional verification parties.
The proof of identity supersedes the approach of proof of work and proof of stake which distribute voting power and rewards to participants according to their investment in some activity or resource and introduces the opportunity to create a universal basic income (UBI) for individuals.
The proof of identity solves the problem with the proof of personhood in which individuals are requested to attend recurrent pseudonymous parties and creates a network that is permanently secured and censorship resilient.
Background
Currently used proofs of investment
In a permission-less network, some kind of proof is required to prevent Sybil attacks, i.e., the event in which an attacker gains control over the transactions of the network by creating multiple users generated with a malicious script.[1]
The most common methods to prevent Sybil attacks are proofs of investment (proof of work, proof of stake) that require participants of the network to invest in some activity or resource as evidence of genuine involvement in the chain.
The growing criticism over this approach is that voting power and rewards are not distributed equally among individuals but instead, big holders/corporations benefit the most from the network.[2] Proof of investment blockchains are thus prone to the formation of oligarchies and marginally appeal to small investors/holders who receive minimal rewards.[3] In the case of proof of work, there are additional sustainability concerns over the amount of electrical energy wasted as proof.[4][5]
The idea of having a "unique identity system" as a consensus protocol for cryptocurrencies, which would give each human user one and only one anti-Sybil participation token, was initially proposed in 2014 by Vitalik Buterin.[6]
The proof of personhood
In contrast with proofs of investment, proof of personhood aims to allocate to each individual one equal unit of voting power and its associated reward.
In the PoP protocol, each individual is required to demonstrate his humanity and uniqueness regardless of his identity by attending a pseudonymous party. To preserve privacy, attendances to parties are anonymous and individuals can wear masks or hide their appearance.[7]
Whilst the PoP protocol achieves the goal of democratizing blockchain networks, some criticisms have been raised over the recurrent nature of PoP parties and more specifically:
- To avoid multiple attendances to pseudonymous parties, each individual has to attend a new party every time the network expands; this suggests the process will be endless or will leave out those individuals unable to attend the last round of parties.[7]
- Because there is no control over the creation of PoP parties and anyone can organize them, more study should be conducted to rule out the possibility for an attacker to create a high number of parties with the intent of populating one or more parties entirely with forgeries and hence gaining a considerable number of minting tokens.[7]
- Because of the recurrent nature of pseudonymous parties, the PoP network does not guarantee the creation of a value stable in time. Any epoch can be better or worse than the previous one, so the network is possibly exposed to censorship and instability.[8]
Other protocols
Some other protocols based on the use of national IDs, online face recognition CAPTCHA solving, and social network identification, have been also proposed; however, in general, they are deemed not secure enough against the threats posed by AI engines’ capacity to create spoofed identities when a banking security level is to be attained.[9][10][11][12][13]
Biometric data-based proofs
The proof of UniqueID
To avoid the problems associated with the recurrent nature of PoP parties and strengthen identification methods against spoofed identities, the use of biometric identification and data storage of individuals/minters were introduced. The first comprehensive study was proposed in June 2018.[14]
According to the white paper, individuals are biometrically identified in person by local verifiers. Then their data are encrypted using a trusted setup and recorded in the blockchain.[14]
The system relies on the Ethereum blockchain for the execution of a set of smart contracts.[14]
The protocol also proposes the use of CAPTCHA parties and the involvement of trusted, famous people to strengthen the system against Sybil attacks.[14]
The proof of UniqueID achieves the goal of assigning one minting token to each identified individual while not requiring attendance to multiple recurrent PoP parties; however, there are some challenges and possible criticisms to consider under this proposal:
- The reliance on the Ethereum blockchain ultimately ties down the security of the system to the security of the Ethereum blockchain and may present serious technical challenges.[7]
- A trusted setup for biometric data encryption may not guarantee the privacy of users against a governmental request of data disclosure. This seems to significantly penalize the censorship resistance of the system.
- There is no certainty against the future possibility that AI engines will be able to solve CAPTCHAs.[10]
- Additional investigation and study may be required to rule out the possibility of carrying out a Sybil attack under this protocol. In fact, it is possible to figure out a scenario in which initial parties are kicked off by a colluding group, or a group of legit verifiers collude with each other and start to generate identity forgeries, particularly in remote locations (e.g., Papua New Guinea).[15] Once spoofed identities successfully infiltrate the system there are no procedures in place to detect them.
The proof of identity
The proof of identity protocol proposes to overcome the possibility of biometric spoofed identities and collusions between participants using an AI engine stored in the blockchain which randomly organizes humanity identification parties and constantly computes the possibility of cheats for each individual/area/country which triggers additional verification parties either in a pyramid scheme or in a random way.[8]
The identification procedure requires each party attendee to perform a face recognition of all others to establish the principle “everyone or no one is cheating,” which ultimately requires attackers to collude globally to avoid being discovered.
The protocol also introduces a new proposal to preserve the privacy of individuals: biometric data are stored partially encrypted. The amount of public data stored in the blockchain is enough to avoid a good number of biometric collisions, but it is not enough to securely identify a person. Once biometric collisions occur, minters are requested by the system to temporarily disclose their encryption key. The system can be implemented according to CanDID methodology.[16]
The proof of identity addresses the problems with the proof of personhood and UniqueID, however, there are some challenges and possible criticisms to consider:
- The amount of data to store in the blockchain is considerable and may require some daily downtime for cohort leader servers to reboot.
- The system includes the creation of a PoID global organization that facilitates the kick-off of identification venues and rules out rare biometric disputes. This may be seen as a center of authority.
Summary of the main protocols based on individuals
The following table summarizes the characteristics of the three main individuals-based protocols:
| Proof of Personhood | Proof of UniqueID | Proof of Identity | |
|---|---|---|---|
| Organization of the parties | By everyone | Initiated by a community of enthusiastic people | Randomly assigned by the AI engine |
| Participation method | Attendance at pseudonymous party | Biometric identification, P2P with some verifiers | Biometric identification, everyone to all, during identification parties |
| Supervision of possible cheats | None | None | Computed by the AI engine, detected by additional verification parties |
| Privacy of participants | Individuals can attend parties in disguise | Data are encrypted on a trusted setup | Data are partially encrypted on a decentralized setup |
| Builds on permanent value | No, every epoch can be better or worse than the previous | Yes | Yes |
| Use cases | Universal basic income | • Universal basic income • Consensus protocol for all blockchains • Voting system |
• Universal basic income • Consensus protocol for all blockchains • Voting system |
| Negatives | Endless process or leaving out those unable to attend last round or parties | • Relying on Ethereum blockchain • Sybil attacks are unlikely but theoretically possible |
• Lots of data to store on the blockchain • the protocol is eased by a global organization, which may be seen as a center of authority |
The proof of identity protocol
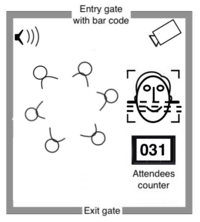
The proof of identity protocol combines state of the art of 3D mapping face recognition technologies, the attendance to humanity identification parties, and the decentralized (stored in the blockchain) supervision of an AI engine that randomly forms parties and carries on organizing additional verification parties to rule out any possible cheating.[8]
The protocol is summarized in the following scheme:
Humanity identification/verification parties are designed in a way to enforce the principle: “everyone or no one is cheating,” ruling out the possibility of having a party formed by honest individuals and spoofed identities at the same time:
- Individuals gather in the identification venue (fig. 1) randomly assigned by the AI engine.
- Individuals are requested to firstly confirm the number of attendees and then to perform the face recognition of all others using their minting app.
- One or more verifiers coming from remote locations attend the party in incognito
Parties kick off in a region once there are enough online data submissions and sufficient interoperability of verifiers. The process includes a public offer to interested “identification entrepreneurs” who are willing to make identification venues available; the PoID global organization facilitates the procedure.[8]
Biometric disputes are very rare in the PoID because the 3D face-mapping technology is able to differentiate close biometric twins, however, the PoID Global Organization is able to rule out rare possible disputes while not constituting a significant center of authority in the system.
Additional verification parties are run by the PoID AI engine to check the status of the ecosystem and by leveraging the principle “everyone or no one is cheating” identity forgeries are discovered by forming verification parties in a pyramid mode, i.e., higher level of parties are made of individuals coming from single lower-level parties. The AI engine also searches for cheats and computes their probability in a random way/outside the principle of “everyone or no one is cheating.”[8]
File:Proof of identity protocol.tif
Use cases for the proof of identity network
The proof of identity consensus protocol has the prerogatives of being:
- Non-quantitative: once the network is sufficiently populated, any blockchain/cryptocurrency can join the network and have its blocks validated by the PoID.
- Permanently secured against Sybil attacks: the PoID security is based on the impossibility for an attacker to create identity forgeries.
- Permanently censorship resilient: because of the high level of distribution and decentralization and the privacy of the minters, the PoID is marginally affected by censorship.
These conditions suggest the possibility for the PoID to become a globally used consensus protocol aggregating all blockchains/cryptocurrencies under the same network.
The second notable use is the creation of a universal basic income for individuals.[17]
A third possible use is to create a direct instrument for democratic participation; in fact, the PoID is made of securely and uniquely identified individuals, which is the necessary requirement to run referendums and surveys.[7][18]
References
- ↑ Douceur, John R. (10 October 2002). "The Sybil Attack". Peer-to-Peer Systems. Lecture Notes in Computer Science. Lecture Notes in Computer Science. 2429. pp. 251–260. doi:10.1007/3-540-45748-8_24. ISBN 978-3-540-44179-3.
- ↑ Fanti, Giulia; Kogan, Leonid; Oh, Sewoong; Ruan, Kathleen; Viswanath, Pramod; Wang, Gerui (18 February 2019). "Compounding of Wealth in Proof-of-Stake Cryptocurrencies". Financial Cryptography and Data Security. Lecture Notes in Computer Science 11598: 42–61. doi:10.1007/978-3-030-32101-7_3. ISBN 978-3-030-32100-0. https://fc19.ifca.ai/preproceedings/161-preproceedings.pdf.
- ↑ Maria, Borge; Kokoris-Kogias, Eleftherios (3 November 2018). "Why Proof-of-Work and Proof-of-Stake Are Undemocratic and Oligarchic". P2P Foundation. https://wiki.p2pfoundation.net/Why_Proof-of-Work_and_Proof-of-Stake_Are_Undemocratic_and_Oligarchic.
- ↑ Bendiksen, Christopher (30 March 2021). "A Closer Look at the Environmental Impact of Bitcoin Mining". https://coinshares.com/research/closer-look-environmental-impact-of-bitcoin-mining.
- ↑ Vorick, David (13 May 2018). "The State of Cryptocurrency Mining". https://blog.sia.tech/the-state-of-cryptocurrency-mining-538004a37f9b.
- ↑ Buterin, Vitalik (25 August 2014). "Problems". https://github.com/ethereum/wiki/wiki/Problems/89fd07ffff8b042134e4ca67a0ce143d574016bd.
- ↑ 7.0 7.1 7.2 7.3 7.4 Maria, Borge; Kokoris-Kogias, Eleftherios; Jovanovic, Philipp; Gasser, Linus; Gailly, Nicolas; Ford, Bryan (3 November 2018). "Proof-of-Personhood: Redemocratizing Permissionless Cryptocurrencies"
- ↑ 8.0 8.1 8.2 8.3 8.4 Andrea, Dalla Val (June 2021). "Proof of Identity White Paper"
- ↑ Pupillo, Lorenzo; Fantin, Stefano; Ferreira, Afonso; Polito, Carolina (May 2021). "Artificial Intelligence and Cybersecurity Technology, Governance and Policy Challenges". Ceps.eu/. https://www.ceps.eu/wp-content/uploads/2021/05/CEPS-TFR-Artificial-Intelligence-and-Cybersecurity.pdf.
- ↑ 10.0 10.1 Choi, Charles Q. (26 October 2017). "Artificial Intelligence Beats CAPTCHA"
- ↑ Assia, Yoni; Bariach, Tomer; Oron, Tal; Stone, Anna; Rottenberg, Hadar; Keinan, Ziv; Ross, Omri; Yaacobi, Nir (28 October 2020). "GoodDollar: A Distributed Basic Income". GoodDollar. https://whitepaper.gooddollar.org/.
- ↑ "Proof-of-personhood". 29 August 2021. https://docs.idena.io/docs/wp/technology.
- ↑ "Universal Proof of Uniqueness". 17 October 2020. https://www.brightid.org/whitepaper.
- ↑ 14.0 14.1 14.2 14.3 Hajialikhani, MohammadJavad; Jahanara, MohammadMahdi (2018). "UniqueID: Decentralized Proof-of-Unique-Human". arXiv:1806.07583 [cs.CR].
- ↑ Siddarth, Divya; Ivliev, Sergey; Siri, Santiago; Berman, Paula (13 October 2020). "Who Watches the Watchmen? A Review of Subjective Approaches for Sybil-resistance in Proof of Personhood Protocols". arXiv:2008.05300 [cs.CR].
- ↑ Maram, Deepak; Malvai, Harjasleen; Zhang, Fan; Jean-Louis, Nerla; Frolov, Alexander; Kell, Tyler; Lobban, Tyrone; Moy, Christine et al. (2021). "CanDID: Can-Do Decentralized Identity with Legacy Compatibility, Sybil-Resistance, and Accountability". IEEE Security & Privacy. https://eprint.iacr.org/2020/934.pdf.
- ↑ Sarah, Allen; Capkun, Srdjan; Eyal, Ittay; Fanti, Giulia; Ford, Bryan; Grimmelmann, James; Juels, Ari; Kostiainen, Kari et al. (23 July 2020). "Design choices for central bank digital currency: Policy and technical considerations". Brookings Institution. https://www.brookings.edu/research/design-choices-for-central-bank-digital-currency-policy-and-technical-considerations/.
- ↑ Ford, Bryan (June 2020). "Technologizing Democracy or Democratizing Technology? A Layered- Architecture Perspective on Potentials and Challenges". Bford.info/. https://bford.info/pub/soc/dt2-chapter.pdf.
 |
 KSF
KSF