Jenkins hash function
 From HandWiki - Reading time: 4 min
From HandWiki - Reading time: 4 min
The Jenkins hash functions are a collection of (non-cryptographic) hash functions for multi-byte keys designed by Bob Jenkins. The first one was formally published in 1997.
The hash functions
one_at_a_time
Jenkins's one_at_a_time hash is adapted here from a WWW page by Bob Jenkins,[1] which is an expanded version of his Dr. Dobb's article.[2] It was originally created to fulfill certain requirements described by Colin Plumb, a cryptographer, but was ultimately not put to use.[1]
uint32_t jenkins_one_at_a_time_hash(const uint8_t* key, size_t length) {
size_t i = 0;
uint32_t hash = 0;
while (i != length) {
hash += key[i++];
hash += hash << 10;
hash ^= hash >> 6;
}
hash += hash << 3;
hash ^= hash >> 11;
hash += hash << 15;
return hash;
}
Sample hash values for one_at_a_time hash function.
one_at_a_time("a", 1)
0xca2e9442
one_at_a_time("The quick brown fox jumps over the lazy dog", 43)
0x519e91f5
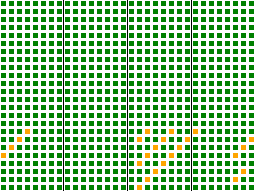
The avalanche behavior of this hash is shown on the right.
Each of the 24 rows corresponds to a single bit in the 3-byte input key, and each of the 32 columns corresponds to a bit in the output hash. Colors are chosen by how well the input key bit affects the given output hash bit: a green square indicates good mixing behavior, a yellow square weak mixing behavior, and red would indicate no mixing. Only a few bits in the last byte of the input key are weakly mixed to a minority of bits in the output hash.
Standard implementations of the Perl programming language prior to version 5.28 included Jenkins's one-at-a-time hash or a hardened variant of it, which was used by default.[3][4]
lookup2
The lookup2 function was an interim successor to one-at-a-time. It is the function referred to as "My Hash" in the 1997 Dr. Dobbs journal article, though it has been obsoleted by subsequent functions that Jenkins has released. Applications of this hash function are found in:
- the SPIN model checker, for probabilistic error detection. In a paper about this program, researchers Dillinger and Manolios note that lookup2 is "a popular choice among implementers of hash tables and Bloom filters". They study lookup2 and a simple extension of it that produces 96-bit rather than 32-bit hash values.[5]
- The Netfilter firewall component of Linux,[6] where it replaced an earlier hash function that was too sensitive to collisions. The resulting system, however, was shown to still be sensitive to hash flooding attacks, even when the Jenkins hash is randomized using a secret key.[7]
- The program that solved the game of kalah used the Jenkins hash function, instead of the Zobrist hashing technique more commonly used for this type of problem; the reasons for this choice were the speed of Jenkins' function on the small representations of kalah boards, as well as the fact that the basic rule of kalah can radically alter the board, negating the benefit of Zobrist's incremental computation of hash functions.[8]
lookup3
The lookup3 function consumes input in 12 byte (96 bit) chunks.[9] It may be appropriate when speed is more important than simplicity. Note, though, that any speed improvement from the use of this hash is only likely to be useful for large keys, and that the increased complexity may also have speed consequences such as preventing an optimizing compiler from inlining the hash function.
The lookup3 function was incorporated into Hierarchical Data Format 5 as a checksum for internal data structures based on its relative strength and speed in comparison to CRC32 and Fletcher32. [10]
SpookyHash
In 2011 Jenkins released a new 128-bit hash function called SpookyHash.[11] SpookyHash is significantly faster than lookup3.
Example for V2 (little-endian x64):
The short method for less than 192 bytes (43 bytes):
Hash128("The quick brown fox jumps over the lazy dog")
2b12e846aa0693c71d367e742407341b
The standard method for more than 191 bytes (219 bytes):
Hash128("The quick brown fox jumps over the lazy dog The quick brown fox jumps over the lazy dog The quick brown fox jumps over the lazy dog The quick brown fox jumps over the lazy dog The quick brown fox jumps over the lazy dog")
f1b71c6ac5af39e7b69363a60dd29c49
See also
- Non-cryptographic hash functions
References
- ↑ 1.0 1.1 Jenkins, Bob (November 3, 2013). "A hash function for hash Table lookup". http://www.burtleburtle.net/bob/hash/doobs.html. Retrieved February 9, 2018.
- ↑ Jenkins, Bob (September 1997). "Hash functions". Dr. Dobb's Journal. https://www.drdobbs.com/database/algorithm-alley/184410284.
- ↑ "RFC: perlfeaturedelta": "one-at-a-time hash algorithm ... [was added in version] 5.8.0"
- ↑ "perl: hv_func.h"
- ↑ Dillinger, Peter C.; Manolios, Panagiotis (2004). "Fast and accurate bitstate verification for SPIN". Proc. 11th International SPIN Workshop. pp. 57–75.
- ↑ Neira Ayuso, Pablo (2006). "Netfilter’s connection tracking system". ;login: 31 (3). http://static.usenix.org/publications/login/2006-06/pdfs/neira.pdf.
- ↑ Bar-Yosef, Noa; Wool, Avishai (2007). "Remote algorithmic complexity attacks against randomized hash tables Proc. International Conference on Security and Cryptography (SECRYPT)". pp. 117–124. https://www.eng.tau.ac.il/~yash/C2_039_Wool.pdf.
- ↑ Irving, Geoffrey; Donkers, Jeroen; Uiterwijk, Jos. "Solving kalah". ICGA Journal. https://naml.us/~irving/papers/irving2000_kalah.pdf.
- ↑ Jenkins, Bob. "lookup3.c source code". http://www.burtleburtle.net/bob/c/lookup3.c. Retrieved April 16, 2009.
- ↑ Koziol, Quincey. "[svn-r12661 Description: · HDFGroup/hdf5@d3a12e1"]. https://github.com/HDFGroup/hdf5/commit/d3a12e1058e9afcb77b265a88690f1d3d5190fd7. Retrieved July 18, 2023.
- ↑ Jenkins, Bob. "SpookyHash: a 128-bit noncryptographic hash". http://www.burtleburtle.net/bob/hash/spooky.html. Retrieved Jan 29, 2012.
 |
 KSF
KSF