Quantum coin flipping
 From HandWiki - Reading time: 14 min
From HandWiki - Reading time: 14 min
Consider two remote players, connected by a channel, that don't trust each other. The problem of them agreeing on a random bit by exchanging messages over this channel, without relying on any trusted third party, is called the coin flipping problem in cryptography.[1] Quantum coin flipping uses the principles of quantum mechanics to encrypt messages for secure communication. It is a cryptographic primitive which can be used to construct more complex and useful cryptographic protocols,[2] e.g. Quantum Byzantine agreement. Unlike other types of quantum cryptography (in particular, quantum key distribution), quantum coin flipping is a protocol used between two users who do not trust each other.[3] Consequently, both users (or players) want to win the coin toss and will attempt to cheat in various ways.[3]
It is known that if the communication between the players is over a classical channel, i.e. a channel over which quantum information cannot be communicated, then one player can (in principle) always cheat regardless of which protocol is used.[4] We say in principle because it might be that cheating requires an unfeasible amount of computational resource. Under standard computational assumptions, coin flipping can be achieved with classical communication.
The most basic figure of merit for a coin-flipping protocol is given by its bias, a number between and . The bias of a protocol captures the success probability of an all-powerful cheating player who uses the best conceivable strategy. A protocol with bias means that no player can cheat. A protocol with bias means that at least one player can always succeed at cheating. Obviously, the smaller the bias better the protocol.
When the communication is over a quantum channel, it has been shown that even the best conceivable protocol can not have a bias less than .[5][6]
Consider the case where each player knows the preferred bit of the other. A coin flipping problem which makes this additional assumption constitutes the weaker variant thereof called weak coin flipping (WCF). In the case of classical channels this extra assumption yields no improvement. On the other hand, it has been proven that WCF protocols with arbitrarily small biases do exist.[7][8] However, the best known explicit WCF protocol has bias .[9]
Although quantum coin flipping offers clear advantages over its classical counterpart in theory, accomplishing it in practice has proven difficult.[3][10]
History
Theory
Manuel Blum introduced coin flipping as part of a classical system in 1983 based on computational algorithms and assumptions.[11] Blum's version of coin flipping answers the following cryptographic problem:
- Alice and Bob are recently divorced, living in two separate cities, and want to decide who gets to keep the car. To decide, Alice wants to flip a coin over the telephone. However, Bob is concerned that if he were to tell Alice heads, she would flip the coin and automatically tell him that he lost.[12]
Thus, the problem with Alice and Bob is that they do not trust each other; the only resource they have is the telephone communication channel, and there is not a third party available to read the coin. Therefore, Alice and Bob must be either truthful and agree on a value or be convinced that the other is cheating.[12]
In 1984, quantum cryptography emerged from a paper written by Charles H. Bennett and Giles Brassard. In this paper, the two introduced the idea of using quantum mechanics to enhance previous cryptographic protocols such as coin flipping.[3] Since then, many researchers have applied quantum mechanics to cryptography as they have proven theoretically to be more secure than classical cryptography, however, demonstrating these protocols in practical systems is difficult to accomplish.
Experiment
As published in 2014, a group of scientists at the Laboratory for Communication and Processing of Information (LTCI) in Paris have implemented quantum coin flipping protocols experimentally.[3] The researchers have reported that the protocol performs better than a classical system over a suitable distance for a metropolitan area optical network.[3]
Definition
Coin flipping
In cryptography, coin flipping is defined to be the problem where two mutually distrustful and remote players want to agree on a random bit without relying on any third party.[13]
Strong coin flipping
In quantum cryptography, strong coin flipping (SCF) is defined to be a coin flipping problem where each player is oblivious to the preference of the other.[14]
Weak coin flipping
In quantum cryptography, weak coin flipping (WCF) is defined to be a coin flipping problem where each player knows the preference of the other.[15]
It follows that the players have opposite preferences. If this were not the case then the problem will be pointless as the players can simply choose the outcome they desire.
Bias
Consider any coin flipping protocol. Let Alice and Bob be the two players who wish to implement the protocol. Consider the scenario where Alice cheats using her best strategy against Bob who honestly follows the protocol. Let the probability that Bob obtains the outcome Alice preferred be given by . Consider the reversed situation, i.e. Bob cheats using his best strategy against Alice who honestly follows the protocol. Let the corresponding probability that Alice obtains the outcome Bob preferred to be given by .
The bias of the protocol is defined to be .
The half is subtracted because a player will get the desired value half the time purely by chance.
Extensions
Coin flipping can be defined for biased coins as well, i.e. the bits are not equally likely. The notion of correctness has also been formalized which requires that when both players follow the protocol (nobody cheats) the players always agree on the bit generated and that the bit follows some fixed probability distribution.
Protocols
Using conjugate encoding
Quantum coin flipping and other types of quantum cryptography communicate information through the transmission of qubits. The accepting player does not know the information in the qubit until he performs a measurement.[12] Information about each qubit is stored on and carried by a single photon.[10] Once the receiving player measures the photon, it is altered, and will not produce the same output if measured again.[10] Since a photon can only be read the same way once, any other party attempting to intercept the message is easily detectable.[10]
Quantum coin flipping is when random qubits are generated between two players that do not trust each other because both of them want to win the coin toss, which could lead them to cheat in a variety of ways.[3] The essence of coin flipping occurs when the two players issue a sequence of instructions over a communication channel that then eventually results in an output.[10]
A basic quantum coin flipping protocol involves two people: Alice and Bob.[11]
- Alice sends Bob a set number of Κ photon pulses in the quantum states . Each of these photon pulses is independently prepared following a random choice by Alice of basis αi and bit ci where i = 1, 2, 3...Κ.
- Bob then measures the pulses from Alice by identifying a random basis βi. Bob records these photons and then reports back the first successfully measured photon j to Alice along with a random bit b.
- Alice reveals the basis and bit that she used at the basis Bob gave her. If the two bases and bits match, then both parties are truthful and can exchange information. If the bit reported by Bob is different than that of Alice's, one is not being truthful.
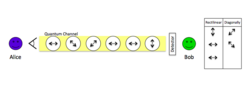
A more general explanation of the above protocol is as follows:[16]
- Alice first chooses a random basis (such as diagonally) and a sequence of random qubits. Alice then encodes her chosen qubits as a sequence of photons following the chosen basis. She then sends these qubits as a train of polarized photons to Bob through the communication channel.
- Bob chooses a sequence of reading bases randomly for each individual photon. He then reads the photons and records the results in two tables. One table is of the rectilinear (horizontal or vertical) received photons and one of the diagonally received photons. Bob may have holes in his tables due to losses in his detectors or in the transmission channels. Bob now makes a guess as to which basis Alice used and announces his guess to Alice. If he guessed correctly, he wins and if not, he loses.
- Alice reports whether he won or not by announcing what basis she used to Bob. Alice then confirms the information by sending Bob her entire original qubit sequence that she used in step 1.
- Bob compares Alice's sequence with his tables to confirm that no cheating occurred on Alice's part. The tables should correspond to Alice's basis and there should be no correlation with the other table.
Assumptions
There are a few assumptions that must be made for this protocol to work properly. The first is that Alice can create each state independent of Bob, and with an equal probability. Second, for the first bit that Bob successfully measures, his basis and bit are both random and completely independent of Alice. The last assumption, is that when Bob measures a state, he has a uniform probability to measure each state, and no state is easier to be detected than others. This last assumption is especially important because if Alice were aware of Bob's inability to measure certain states, she could use that to her advantage. [11]
Cheating
The key issue with coin flipping is that it occurs between two distrustful parties.[16] These two parties are communicating through the communication channel some distance from each other and they have to agree on a winner or loser with each having a 50 percent chance of winning.[16] However, since they are distrustful of one another, cheating is likely to occur. Cheating can occur in a number of ways such as claiming they lost some of the message when they do not like the result or increasing the average number of photons contained in each of the pulses.[3]
For Bob to cheat, he would have to be able to guess Alice's basis with a probability greater than ½.[16] In order to accomplish this, Bob would have to be able to determine a train of photons randomly polarized in one basis from a train of photons polarized in another basis.[16]
Alice, on the other hand, could cheat in a couple of different ways, but she has to be careful because Bob could easily detect it.[16] When Bob sends a correct guess to Alice, she could convince Bob that her photons are actually polarized the opposite of Bob's correct guess.[16] Alice could also send Bob a different original sequence than she actually used in order to beat Bob.[16]
Detecting a third-party
Single photons are used to pass the information from one player to the other (qubits).[10] In this protocol, the information is encoded in the single photons with polarization directions of 0, 45, 90, and 135 degrees, non-orthogonal quantum states.[16] When a third party attempts to read or gain information on the transmission, they alter the photon's polarization in a random way that is likely detected by the two players because it does not match the pattern exchanged between the two legitimate users.[16]
The Dip Dip Boom protocol (weak coin flipping with bias )
The Dip Dip Boom (DDB) protocol is a quantum version of the following game.[17] Consider a list of numbers , each between 0 and 1. The players, Alice and Bob, take turns to say "Dip" or "Boom" with probability at round . The player who says "Boom" wins. Obviously, a cheating player can simply say "Boom" and win as there are no rewards for longer games. We will consider games that terminate so that for some (large) , say , we set .
Consider round . Let us denote by and the probability of, respectively, Alice and Bob winning. Let be the probability that the game remains undecided. These numbers for the classical game described above can be evaluated inductively.
We now describe the quantum version. Let be a three dimensional Hilbert space spanned by . Let be a two dimensional Hilbert space which is spanned by .
- Initialisation: Alice holds the registers and initialises the state to . Bob holds the register and initialises it to the state .
- Iteration: For to the following must be performed. For odd we set X=A (for Alice) and Y=B (for Bob); for even we set X=B and Y=A.
- X implements the operation .
- X sends the message register to Y.
- Y implements the operation .
- Y measures the message register in the computational basis. If the outcome is BOOM then Y aborts and declares him/herself the winner.
- Measurement: Alice and Bob both measure their local register and respectively. If the outcome is U then they declare themselves to be the winner. If the outcome is A then Alice is the winner and for B it is Bob.
Remarks
- To obtain a balanced protocol one must choose the s such that .
- If both players follow the protocol, i.e. no player cheats, then the outcome at the end of step two will never be BOOM and neither will the outcome at step 3 be .
- The bias analysis of this protocol uses SDP duality.
- For large the bias of the protocol can be made arbitrarily close to .
Optimal strong coin flipping
It has been shown that using a WCF protocol with an arbitrarily small bias one can construct a SCF protocol with bias arbitrarily close to which is known to be optimal.[18]
Experimental implementation
Using conjugate encoding
As mentioned in the history section, scientists at the LTCI in Paris have experimentally carried out a quantum coin flipping protocol. Previous protocols called for a single photon source or an entangled source to be secure. However, these sources are why it is difficult for quantum coin flipping to be implemented. Instead, the researchers at LTCI used the effects of quantum superposition rather than a single photon source, which they claim makes implementation easier with the standard photon sources available.[3]
The researchers used the Clavis2 platform developed by IdQuantique for their protocol, but needed to modify the Clavis2 system in order for it to work for the coin flipping protocol. The experimental setup they used with the Clavis2 system, involves a two-way approach. Light pulsed at 1550 nanometres is sent from Bob to Alice. Alice then uses a phase modulator to encrypt the information. After encryption, she then uses a Faraday mirror to reflect and attenuate the pulses at her chosen level and sends them back to Bob. Using two high quality single photon detectors, Bob chooses a measurement basis in his phase modulator to detect the pulses from Alice.[11]
They replaced the detectors on Bob's side because of the low detection efficiencies of the previous detectors. When they replaced the detectors, they were able to show a quantum advantage on a channel for over 15 kilometres (9.3 mi). A couple of other challenges the group faced was reprogramming the system because photon source attenuation was high and performing system analyses to identify losses and errors in system components. With these corrections, the scientists were capable of implementing a coin flipping protocol by introducing a small honest abort probability, the probability that two honest participants cannot obtain a coin flip at the end of the protocol, but at a short communication distance.[3]
References
- ↑ Blum, Manuel (1983-01-01). "Coin flipping by telephone a protocol for solving impossible problems". ACM SIGACT News 15 (1): 23–27. doi:10.1145/1008908.1008911. ISSN 0163-5700.
- ↑ Oded., Goldreich (2003). Foundations of cryptography. Cambridge, UK: Cambridge University Press. ISBN 9780521791724. OCLC 45093786.
- ↑ 3.00 3.01 3.02 3.03 3.04 3.05 3.06 3.07 3.08 3.09 Stuart Mason Dambort, "Heads or tails: Experimental quantum coin flipping cryptography performs better than classical protocols", Phys.org, March 26, 2014
- ↑ Cleve, R. (1986-11-01). "Limits on the security of coin flips when half the processors are faulty". Proceedings of the eighteenth annual ACM symposium on Theory of computing - STOC '86. ACM. pp. 364–369. doi:10.1145/12130.12168. ISBN 0897911938. http://dl.acm.org/citation.cfm?id=12130.12168.
- ↑ A. Kitaev, Quantum Coin Flipping, Quantum Information Processing Workshop, Mathematical Sciences Research Institute, University of California, Berkeley, 2003.
- ↑ Ambainis, A.; Buhrman, H.; Dodis, Y.; Rohrig, H. (2004). "Multiparty quantum coin flipping". Proceedings. 19th IEEE Annual Conference on Computational Complexity, 2004. IEEE. pp. 250–259. doi:10.1109/ccc.2004.1313848. ISBN 0769521207. https://ieeexplore.ieee.org/document/1313848.
- ↑ C. Mochon, Quantum Weak Coin Flipping with Arbitrarily Small Bias, preprint, arXiv:0711.4114, 2007.
- ↑ Aharonov, Dorit; Chailloux, André; Ganz, Maor; Kerenidis, Iordanis; Magnin, Loïck (January 2016). "A Simpler Proof of the Existence of Quantum Weak Coin Flipping with Arbitrarily Small Bias". SIAM Journal on Computing 45 (3): 633–679. doi:10.1137/14096387x. ISSN 0097-5397.
- ↑ Mochon, Carlos (2005). "Large family of quantum weak coin-flipping protocols". Physical Review A 72 (2): 022341. doi:10.1103/PhysRevA.72.022341. Bibcode: 2005PhRvA..72b2341M.
- ↑ 10.0 10.1 10.2 10.3 10.4 10.5 Vivek R and Dr. J. Roopchand, “Emerging Trends in Quantum Cryptography – A Survey", International Journal of Computer Technology and Applications, August 2012
- ↑ 11.0 11.1 11.2 11.3 Anna Pappa et al., "Experimental Plug and Play Quantum Coin Flipping", Nature Communications, April 24, 2014
- ↑ 12.0 12.1 12.2 C. Döscher and M. Keyl, "An Introduction to Quantum Coin-Tossing", Cornell University Library, February 1, 2008
- ↑ Blum, Manuel (1983-01-01). "Coin flipping by telephone a protocol for solving impossible problems". ACM SIGACT News 15 (1): 23–27. doi:10.1145/1008908.1008911. ISSN 0163-5700.
- ↑ D. Aharonov, A. Ta-Shma, U. V. Vazirani, and A. C. Yao, Quantum bit escrow, in Proceedings of the 32nd Annual ACM Symposium on Theory of Computing, ACM, New York, 2000, pp. 705–714.
- ↑ Spekkens, R. W. (2002). "Quantum Protocol for Cheat-Sensitive Weak Coin Flipping". Physical Review Letters 89 (22): 227901. doi:10.1103/PhysRevLett.89.227901. PMID 12485105. Bibcode: 2002PhRvL..89v7901S.
- ↑ 16.00 16.01 16.02 16.03 16.04 16.05 16.06 16.07 16.08 16.09 Charles H. Bennett and Giles Brassard, "Quantum cryptography: Public key distribution and coin tossing", Theoretical Computer Science, December 4, 2014
- ↑ Mochon, Carlos (2005). "Large family of quantum weak coin-flipping protocols". Physical Review A 72 (2): 022341. doi:10.1103/PhysRevA.72.022341. Bibcode: 2005PhRvA..72b2341M.
- ↑ 50th Annual IEEE Symposium on Foundations of Computer Science, 2009 FOCS '09 ; 25-27 Oct. 2009, Atlanta, Georgia, USA ; proceedings. IEEE Computer Society Technical Committee on Mathematical Foundations of Computing, Annual IEEE Symposium on Foundations of Computer Science 50 2009.10.25-27 Atlanta, Ga., FOCS 50 2009.10.25-27 Atlanta, Ga.. Piscataway, NJ. 2009. ISBN 9781424451166. OCLC 838170374.
 |
 KSF
KSF