Linux Malware Detect
Topic: Software
 From HandWiki - Reading time: 3 min
From HandWiki - Reading time: 3 min
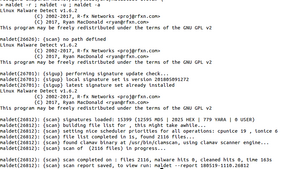 Output of a sample run of LMD | |
| Developer(s) | R-fx Networks |
|---|---|
| Stable release | 1.6.4
/ March 18 2019 |
| Operating system | Linux |
| Type | Linux malware Detector |
| License | GNU GPL v2 |
| Website | www |
Linux Malware Detect, abbreviated as LMD or maldet, is a software package that looks for malware on Linux systems and reports on it.[1]
Details
To protect Linux systems against vulnerabilities, various software packages are available, such as rootkit detectors such as Rootkit Hunter and chkrootkit, and auditing systems like lynis. Malware detection software such as LMD and ClamAV improve the security of systems by scanning them based on the signatures of thousands of instances of known malware.
For malware signatures, LMD uses various sources such as the signatures database of ClamAV and the Malware Hash Registry of Team Cymru.[2][3] Besides such third party signature databases, it also maintains its own database of signatures.
If a ClamAV scanner engine is already available on a system, LMD will use this for its scanner engine. This will normally give better performance than its built-in scanner engine.[1]
LMD can quarantine malware, and it can clean software that contains malicious code.[4]
The executable command of LMD is maldet. Typical command invocations are maldet -d, to check for later versions; maldet -u, to check for malware signature updates; and maldet -a, to scan the file system of the server on which LMD resides. Checking for malware signature updates is typically done in an automated manner. Besides periodic scans, real-time monitoring is also supported with the --monitor command-line argument. LMD can monitor users, paths and files in such a way.[4]
Linux Malware Detect is one of the objectives for the LPI 303 certification.[5]
References
- ↑ 1.0 1.1 Mastering Linux Security and Hardening by Donald A. Tevault Publisher: Packt Publishing Release Date: January 2018 ISBN 9781788620307
- ↑ Linux Server Security, Chapter 8 Malware Detection, by Chris Binnie, John Wiley & Sons, 2016, ISBN 9781119277651
- ↑ Cymru, Team. "Malware Hash Registry - Team Cymru". https://www.team-cymru.com/mhr.html. Retrieved 19 May 2018.
- ↑ 4.0 4.1 "Linux Malware Detect - R-fx Networks". https://www.rfxn.com/projects/linux-malware-detect/. Retrieved 19 May 2018.
- ↑ "Exam 303 Objectives". 31 August 2016. https://www.lpi.org/our-certifications/exam-303-objectives. Retrieved 19 May 2018.
External links
 |
 KSF
KSF