FDIC Enterprise Architecture Framework
 From Wikipedia - Reading time: 6 min
From Wikipedia - Reading time: 6 min
This article's factual accuracy may be compromised due to out-of-date information. (January 2013) |

FDIC Enterprise Architecture Framework was the enterprise architecture framework of the United States Federal Deposit Insurance Corporation (FDIC). A lot of the current article is about the enterprise architecture framework developed around 2005, and currently anno 2011 out-of-date.[citation needed]
Overview
[edit]The FDIC's framework for implementing its Enterprise Architecture was based on Federal and industry best practices, including the Chief Information Officer (CIO) Council's Federal Enterprise Architecture Framework (FEAF) and the Zachman Framework for Enterprise Architecture. FDIC's framework was tailored to emphasize security. The historic FDIC EA framework complies with the FEAF and highlights the importance of security to all other components of the architecture.[2]
The FDIC EA framework included five components. The first component, the Business Architecture, focused on FDIC's business needs. The next three components, the Data Architecture, Applications Architecture, and Technical Infrastructure Architectures, focused on the technological capabilities that support the business and information needs. The final component, the Security Architecture, focused on specific aspects of interest to the Corporation that span the enterprise and must be integral parts of all other architectures.[2]
History
[edit]Historically, Federal agencies managed IT investments autonomously. Until the new millennium, there was little incentive for agencies to partner to effectively reuse IT investments, share IT knowledge, and explore joint solutions. Starting in the second half of 1990 a collective, government-wide effort, supported by the Federal CIO Council, utilizing the Federal Enterprise Architecture (FEA), was undertaken in an effort to yield significant improvements in the management and reuse of IT investments, while improving services to citizens, and facilitating business relationships internally and externally.[3]
The Federal Deposit Insurance Corporation (FDIC) first realized the value of Enterprise Architecture in 1997, when two business executives had to reconcile data that had come from different systems for a high-profile report to the banking industry. The FDIC's first EA blueprint was published in December 2002.[4]
In 2004 the FDIC received a 2004 Enterprise Architecture Excellence Award from the Zachman Institute for Framework Advancement (ZIFA) for its initiative to manage corporate data collaboratively.[5]
EA framework topics
[edit]Historical FDIC EA framework
[edit]The FDIC EA framework from 2005 included five components.
- Business Architecture : The Business Architecture described the activities and processes performed by the corporation to achieve its mission and to realize its vision and goals. Developing the Business Architecture was the first step in creating an Enterprise Architecture (EA) that linked the corporation's business needs to its Information Technology (IT) environment. Maximizing IT support for these requirements was intended to optimize Corporate performance.[2]
- Data Architecture : The Data Architecture described the activities required to obtain and maintain data that support the information needed by the corporation's major business areas. Data and information are different. Data is the foundation of information. Data is the raw material that is processed and refined to generate information. Information consists of a collection of related data that has been processed into a form that is meaningful to the recipient.[2]
- Applications Architecture : The Applications Architecture described the major types of applications that manage data to produce the information needed to support the activities of the corporation. The Applications Architecture provided a framework that enabled the migration from the applications catalog and software development environment in use at the time to the target integrated applications, development and engineering environments. The target architecture promoted the use of commercial and government off-the-shelf products, consolidating applications, where applicable, and the use of emerging technologies where appropriate.[2]
- Technical Infrastructure Architecture : The IT infrastructure provided access to application systems and office automation tools used in performance of the business processes. The Corporation placed high priority on maintaining a consistent, available, and reliable technical infrastructure. The Technical Architecture described the underlying technology for the corporation's business, data, and application processing. It included the technologies used for communications, data storage, application processing, and computing platforms.[2]
- Security Architecture : The Security Architecture established a framework for integrating safeguards into all layers of the FDIC's Enterprise Architecture. The security architecture used a risk management and information assurance strategy that provides access control, confidentiality, integrity, and non-repudiation for the corporation's information and systems.[2]
Self-Funding Model for Reinvestment in IT
[edit]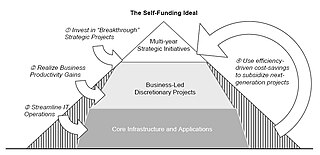
The banking business model of 2008 had become more complex, giving rise to financial instruments such as collateralized debt obligations (CDOs) and structured investment vehicles (SIVs) to manage risk. These instruments created greater dependencies between the domestic and international financial markets. Financial institutions of that time should have, therefore, struck a balance between regulatory, legislative and banker concerns while appropriately managing risk.[6]
Notionally, as cost savings are realized from a simplified IT environment and more efficient processes, the savings can be reinvested for IT improvements or accrue to the corporation. This self-funding model is shown on the right.[6]
2008 - 2013 technology roadmap
[edit]The technology roadmap outlined the major initiatives for standardizing the IT environment and increasing IT's efficiency and effectiveness over five years. The initiatives were determined by various sources including business-side IT roadmaps, executive management planning meetings, client planning sessions, and client year-end reviews. The three major initiatives identified were enterprise architecture, security and privacy programs, and fiscal discipline.[6]
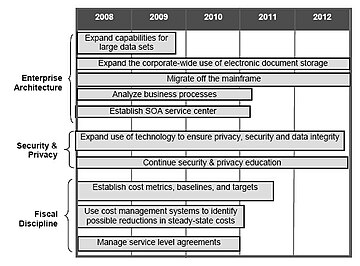
The enterprise architecture initiative focused on simplifying the environment to ensure stable and economical performance for mission-critical applications. Simplifying the environment to decrease costs included activities, such as decreasing the number of application systems and migrating applications off the mainframe. Efficiencies were also hoped to be gained by expanding capabilities for manipulating large data sets and storing traditional paper-based files electronically. The SOA service center was intended to manage code (or services) for all development teams to discover and use, which was expected to save time and costs in application development, testing and deployment.[6]
The organization planned to continue to enhance IT security and privacy programs to address new and evolving risks by improving controls over sensitive data. In some cases, technology, such as scanning outgoing e-mail for sensitive information and encrypting removable storage devices, could mitigate potential risks. The other cornerstone of mitigating risk was educating employees of emerging security and privacy issues.[6]
Lastly, in order to continue sound fiscal discipline and responsibility, the organization planned to establish IT baselines and metrics, study steady-state costs, manage service level agreements, and more judiciously choose new development projects. These three areas – enterprise architecture, security and privacy programs, and fiscal discipline – are shown below with the estimated time frames.[6]
See also
[edit]References
[edit]- ^ OIG (2005). Implementation of E-Government Principles Archived 2009-01-14 at the Wayback Machine. May 2005
- ^ a b c d e f g Implementation of E-Government Principles Archived 2009-01-14 at the Wayback Machine AUDIT REPORT, Report No. 05-018, May 2005
- ^ FDIC (2003). Information Technology Strategic Plan 2004–2007 Archived 2009-04-22 at the Wayback Machine
- ^ Gregg Kreizman, Cathleen E. Blanton (2005) "The FDIC Is Aligning IT to Business Through Enterprise Architecture Archived 2009-03-20 at the Wayback Machine" Gartner, Inc.
- ^ FDIC Receives Technology Award
- ^ a b c d e f g CIO Council (2008) Information Technology Strategic Plan 2008–2013, January 23, 2008. Archived January 3, 2011, at the Wayback Machine
Further reading
[edit]- Gartner (2005) The FDIC Is Aligning IT to Business Through Enterprise Architecture. Industrial research paper.
- Pallab Saha (2007). Handbook of Enterprise Systems Architecture in Practice. Chapter IX gives a detailed case study of the FDIC.
External links
[edit]- FDIC Homepage.
 KSF
KSF