Internet Crime
 From Conservapedia
From Conservapedia Internet Crime is directly related to online or Internet misuse and/or abuse. Some are variations on older schemes of a non-Internet nature, adapted for use on the Net.
Contents
Criminal Statutes Governing the Internet[edit]
Here are federal laws criminalizing wrongful internet activity in the United States:
- 15 USC §§ 7701–7713, Controlling Assault of Non-Solicited Pornography and Marketings Act of 2003 (CAN-SPAM Act)
- 18 USC § 1029, prohibits fraud and related activity using access devices
- 18 USC § 1030, prohibits destructive activity, punishable by up to 10 years in jail ("Computer Fraud and Abuse Act")
- 18 USC § 1030(a)(5)(A) Knowingly transmitting a program, script, or code that would cause damage to a protected computer
- 18 USC § 1343, prohibits wire fraud
- 18 USC § 1361–2, prohibits malicious mischief
- 18 USC § 1470, prohibits unwanted obscenity, punishable by up to 10 years in jail
- 18 USC § 1951, prohibits interfering with commerce by threats or violence
- 18 USC § 2314, prohibits interstate transport of improperly obtained materials[1]
- 18 USC § 2510–11, prohibits interception of electronic communications ("Electronic Communications Privacy Act", "ECPA")
- 18 USC § 2701, prohibits access to information stored on a computer
Most states also have their own laws making it a crime to access a computer or network without the permission of the owner. A table of each state law prohibiting unauthorized access is available from the National Conference of State Legislatures.[2] The following are some examples.
- In August 2008, the governor signed into law Senate Bill 2426 (known as "The Cyberbullying Law"). The bill had overwhelmingly passed in both the House and Senate, each of which had only one "nay" vote. "This law clarifies the definition of harassing someone by using electronic communication such as the Internet and text messaging and enables the prosecution of someone who anonymously bullies in this capacity. SB 2426 becomes law January 1, 2009." Since 2007 Illinois has had the Illinois State Police (ISP) Internet Crimes Unit, and it had received over 100 complaints of cyber-stalking in little more than year. Since 2006 Illinois has had the Internet Crimes Unit (ICU),[3] which coordinates investigations.[4]
- "The bill updates state laws against harassment by removing the requirement that the communication be written or over the telephone. Supporters say the bill now covers harassment from computers, text messages and other electronic devices."[7]
- N.Y. Penal Law § 156.00 to 156.50
Ohio:
- ORC §2913.04 ("Unauthorized use of computer or telecommunication property")
- ORC §2917.21 ("Telecommuncation harassment")
Other states that have similar laws, and where arrests have been made, include:
Successful prosecutions[edit]
- "Ms. Drew could face up to three years in prison and $300,000 in fines" for her conviction on "three misdemeanor charges of computer fraud for her involvement in creating a phony account on MySpace to trick a teenager." "If you are going to attempt to annoy or go after a little girl and you're going to use the Internet to do so," the federal prosecutor said, "this office and others across the country will hold you responsible."[8]
- Up to "a total of 60 years in prison and fines of $1.75 million" face botnet user John Schiefer, convicted of 4 felonies for "accessing protected computers, disclosing illegally intercepted electronic communications, wire fraud and bank fraud." Some of his accomplices were teenagers.[9]
- "A federal jury in Phoenix, Arizona convicted Jeffrey Kilbride, 41, of Venice, California and James Schaffer, 41 of Paradise Valley, Arizona of eight counts, including conspiracy, fraud, money laundering, and transportation of obscene materials. ... They face up to five years in jail for each spam and obscenity offense and a fine of up to $500,000 and up to 20 years for money laundering. They will be sentenced in September" 2007.[10]
- Robert Morris was a graduate student in computer science at Cornell University who released his worm on the internet on Nov. 2, 1988. In 1990, Morris was convicted of violating 18 USC § 1030. He appealed, and his conviction was affirmed in U.S. v. Morris, 928 F.2d 504 (2d Cir. 1991). He petitioned the Supreme Court but it had better things to do, and it denied cert. in 502 U.S. 817 (1991).
- Many more convictions, including the first successful prosecution of a bot attack, can be found here: http://www.cybercrime.gov/cccases.html
Pending Charges[edit]
A 19-year-old resident of the State of Washington named Randy Travis, who used an online name of "fireismyplaymate" was charged "with five felonies after using a computer hacking-scheme to falsely report a homicide in California." If convicted, he faces up to 18 years in jail.[11]
Two college students face a $250,000 fine and 20 years in jail for their "unauthorized computer access, identity theft, conspiracy, and wire fraud" in misusing the school computer. They changed their grades in the school computer.[12]
Other rules[edit]
Most schools, employers and internet service providers (ISPs) prohibit misuse of their computers, and disciplinary action can be expected by those who harassing others or vandalize websites using someone else's property. For example, the University of Cincinnati has a strict policy against misuse of its system.[13]
Libel:
- Publication of false information that is injurious to the reputation of another is called libel and can be the basis of a lawsuit for damages. Internet communications (web pages and postings to newsgroups or mailing lists) are considered publications.
INFORMATION TECHNOLOGY, MISUSE OF:
Theft, misuse or illegal use of information technology such as computer hardware or software, electronic mail or information, voice mail, telephone, fax, including but not limited to:
- Unauthorized entry into a file to use, read or change the contents, or for any other purpose.
- Unauthorized transfer or distribution of a file.
- Unauthorized use of another individual’s identification and password.
- Use of information technology to interfere with the work of another student, faculty member, or University official or with normal operations of the University.
- Use of information technology for unauthorized posting of copyrighted materials or obscenities"
Computer Crime & Intellectual Property Section United States Department of Justice[edit]
Reporting Computer Hacking, Fraud and Other Internet-Related Crime:
The primary federal law enforcement agencies that investigate domestic crime on the Internet include: the Federal Bureau of Investigation (FBI), the United States Secret Service, the United States Immigration and Customs Enforcement (ICE), the United States Postal Inspection Service, and the Bureau of Alcohol, Tobacco and Firearms (ATF) . Each of these agencies has offices conveniently located in every state to which crimes may be reported. Contact information regarding these local offices may be found in local telephone directories. In general, federal crime may be reported to the local office of an appropriate law enforcement agency by a telephone call and by requesting the "Duty Complaint Agent."
Each law enforcement agency also has a headquarters (HQ) in Washington, D.C., which has agents who specialize in particular areas. For example, the FBI and the U.S. Secret Service both have headquarters-based specialists in computer intrusion (i.e., computer hacker) cases.[14]
The Internet Crime Complaint Center[edit]
The Internet Crime Complaint Center (IC3) was established as a partnership between the Federal Bureau of Investigation (FBI) and the National White Collar Crime Center (NW3C) to serve as a means to receive Internet related criminal complaints and to further research, develop, and refer the criminal complaints to federal, state, local, or international law enforcement and/or regulatory agencies for any investigation they deem to be appropriate. The IC3 was intended, and continues to emphasize, serving the broader law enforcement community to include federal, as well as state, local, and international agencies, which are combating Internet crime and, in many cases, participating in Cyber Crime Task Forces.
Since its inception, the IC3 has received complaints crossing the spectrum of cyber crime matters, to include online fraud in its many forms including Intellectual Property Rights (IPR) matters, Computer Intrusions (hacking), Economic Espionage (Theft of Trade Secrets), Online Extortion, International Money Laundering, Identity Theft, and a growing list of Internet facilitated crimes. Since June 2000, it has become increasingly evident that, regardless of the label placed on a cyber crime matter, the potential for it to overlap with another referred matter is substantial. Therefore, the IC3, formerly known as the Internet Fraud Complaint Center (IFCC), was renamed in October 2003 to better reflect the broad character of such matters having an Internet, or cyber, nexus referred to the IC3, and to minimize the need for one to distinguish "Internet Fraud" from other potentially overlapping cyber crimes.
IC3 Mission Statement
- IC3's mission is to serve as a vehicle to receive, develop, and refer criminal complaints regarding the rapidly expanding arena of cyber crime. The IC3 gives the victims of cyber crime a convenient and easy-to-use reporting mechanism that alerts authorities of suspected criminal or civil violations. For law enforcement and regulatory agencies at the federal, state, local, and international level, IC3 provides a central referral mechanism for complaints involving Internet related crimes.
- Significant and supplemental to partnering with law enforcement and regulatory agencies, it will remain a priority objective of the IC3 to establish effective alliances with industry. Such alliances will enable the IC3 to leverage both intelligence and subject matter expert resources, pivotal in identifying and in crafting an aggressive, proactive approach to combating cyber crime.[15]
See also[edit]
- Chinese Cyberterrorism
- A.V. v. iParadigms
- EF Cultural Travel BV v. Explorica
- United States v. Schuster (jail time for perpetrator of "denial of service" attacks)
References[edit]
- ↑ This applies to computer data files U.S. v. Riggs, 739 F.Supp. 414 (N.D.Ill 1990).
- ↑ http://www.ncsl.org/programs/lis/CIP/hacklaw.htm
- ↑ http://www.isp.state.il.us/icu
- ↑ http://illinoischannel.spaces.live.com/?_c11_BlogPart_pagedir=Previous&_c11_BlogPart_handle=cns!B0DB128F5CD96151!3845&_c11_BlogPart_BlogPart=blogview&_c=BlogPart
- ↑ http://www.legislature.mi.gov/(S(vjums4ac12pjz555m2jvvk55))/mileg.aspx?page=getObject&objectName=mcl-752-795
- ↑ http://news.com.com/8301-10784_3-9722006-7.html
- ↑ https://edition.cnn.com/2008/TECH/07/01/cyberbullying.ap/index.html?eref=rss_tech
- ↑ [1]
- ↑ [2]
- ↑ http://www.theregister.co.uk/2007/06/26/can_spam_convictions/
- ↑ [3]
- ↑ [4]
- ↑ http://www.uc.edu/ucit/ITpolicydefs.asp#fedlaw
- ↑ http://www.usdoj.gov/criminal/cybercrime/reporting.htm
- ↑ http://www.ic3.gov/about/
Categories: [United States Law] [Internet Crime] [Crime] [Internet] [United States Department of Justice] [Police State]
↧ Download as ZWI file | Last modified: 02/24/2023 10:28:02 | 165 views
☰ Source: https://www.conservapedia.com/Internet_Crime | License: CC BY-SA 3.0
 ZWI signed:
ZWI signed: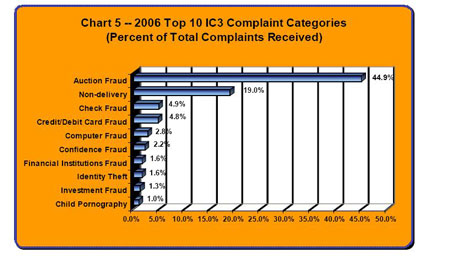
 KSF
KSF